cloudium
One Powerful Solution For All Your Data Needs !!!
The product proper for our firm, which prevents the document from being loss and lost, and manages the document systematically.
H/W, S/W integrated, Plug-and-Play appliance package, document centralization ‘cloudium’
Introduction of cloudium
It gathers all documents in the company to the in-house cloud server easily and simply, and confirms the document anywhere in PC/mobile.
cloudium is our firm’s document centralization cloud server which safely manages the document asset although the employee transfers to another department or leaves the company. Irreplaceable document centralization solution, charm of cloudium
Irreplaceable document centralization solution, charm of cloudium
Function of cloudium which is beneficial to your business

cloudium is the solution to the attack by malignant APT like the ransomware!
It protects the data kept in cloudium by the security technology of total 3 stages.
Step 1: Allowing only the process approved through the sandbox space to gain access
cloudium creates a sandbox(virtual security space) in the user local during the paperwork and downloads the document there for work. Sandbox allows only the access of the process(white list) approved by the administer and blocks the access of the unauthorized process like the ransomware.
Step2: Work performance through the proxy file during the server file work
cloudium does not directly modify the file in the server storage when modifying the document but modify by downloading the file to the sandbox space in of local, so the direct access to the original document kept in the server is blocked. So it is impossible to transform or encrypt the original document by the ransomware.
Step3: Safe file management structure
cloudium uses the version structure when saving the document. Even if the ransomware infects the document in the sandbox space by using the security weak point of the process permitting the ransomware and saves it in the server storage, cloudium can restore quickly to the state before being infected because of the version management structure.

cloudium can protect the critical data and manage it systematically at one go!
You can check easily through the version/history management in cloudium.
You can confirm when who delivered the document where and where he or she downloaded the external link. You can know when who modified through the version management and can also confirm the content before modification.
The administer can check who delivered what document to the outside, what the reason is, the amount of documents registered in the system, and agent connection sate by connecting to the administer page. cloudium can set the document right in the folder differently. You can set the document right depending on the importance in one folder without making several folders in the department onerously and manage.
Give the right when necessary and cancel the right when unnecessary. Proceed with the business freely by cloudium!
When you want to know how who delivers what document of your firm to the outside but there is no way
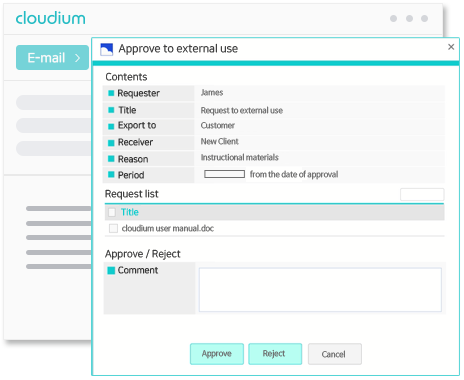
History management which can trace easily and external carrying-out approval process!
You can choose the approval or return before sharing the document with the outside through the external carrying-out approval process provided by cloudium.
As you can set in detail the reading period, reading number, password, and maximum number of available PC, you can share more safely. You can reduce the risk that the document is leakaged indiscreetly a lot just by confirming when why one shares the document with whom in advance.
In addition, you can easily check the external carrying-out history of critical document, modification history, inquiry history, and sharing history by the history management.

DRM which prevents the leakage by encrypting the document, DLP which prevents the document leakage by controlling the spill route, and backup solution which restores the document file when it is damaged or swept away. Although it is necessary to introduce the security solutions of which use is different each to manage the critical document in the organization safely, the cost for introduction is expensive and it is hard to manage and maintain the system. Since DRM and DLP save the document in the personal PC domain not the server storage, it is hard to cooperate through the document sharing and to make the document in the firm into an asset.
What is necessary at this time is cloudium!
Since cloudium saves the document by encrypting in the server storage and manages the lifecycle of the document ranging from the writing to the modification and disuse, it can trace when a sudden accident happens. Since the administer approval is surely necessary when taking out the document, there is no risk that the file is spilled by means of the external storage device like USB or external hard disk.
Also, it is possible to restore to the latest document by the version management function when the document is damaged or wrongly modified. Since the all necessary documents for the organization are saved in cloudium systematically, you can attain the purpose of making the document an asset.
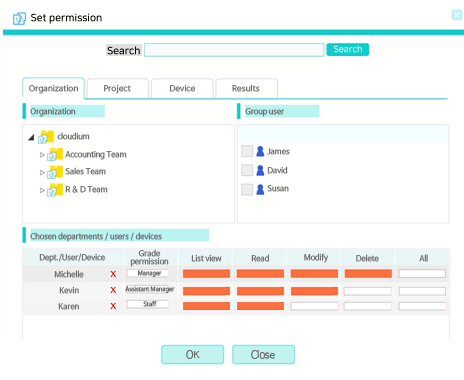
Section chief Kim from the management support room of a social commerce company was ordered to find a way to safely and systematically manage the confidential document on which the customers’ personal information or restricted document are written. As the issue about the corporate internal information spill which is getting serious day by day does not subside, the boss seems to feel anxious. Since he saves and manages the document through the personal PC and network drive, the problem that internal staff spills the document easily happens often and the problem that critical documents were exposed easily when outside people visited the company happened too, section chief Kim’s worry deepens more.
Solve easily and smartly by the access right function of cloudium!
cloudium can set the right in detail by the user, rank, and document.
As for the really critical document, you can set only for people really needing the document to gain access to the pertinent folder and the document by the access right setting. You can also manage the matters on when what who did by the history in the system.
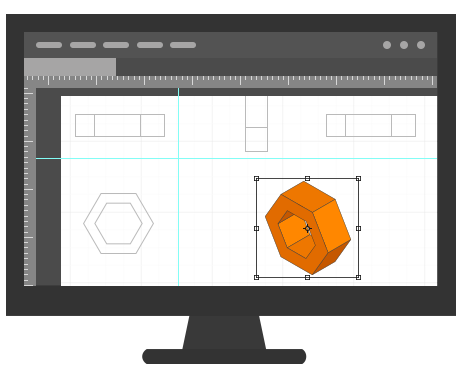
cloudium can manage the bulk data like the floorplan!!
If you manage all the floor plans which were managed by individual staff by registering in cloudium, you can manage the consistent version of floor plan and the history. It is very simple to refer to other coworkers’ floor plans by the access right. However big the floor plan file is, you can transmit to the file URL so you can share safely and simply and use freely.
cloudium provides the security drive which facilitates the fast work by the local PC use speed in the light of the stuffy network environment problem and the onerousness of uploading and downloading to the server storage whenever modifying the bulk file.
In addition, you can prevent the document created in the security drive from being taken out to the outside without the approval according to the in-house document security policy and can work efficiently because you can preview the file by thumbnail.
cloudium helps with take-over and hand-over quickly.
You no longer need to write the taking-over manual and take over the work through the USB, email, and paper! Proceed with easy and exact taking-over by cloudium~
If a new member has come, share the work by giving only the right of the assigned division/team folder! You only have to change the yielder’s folder possessor into the accepter.
Start the speedy taking-over done by one click by means of cloudium.
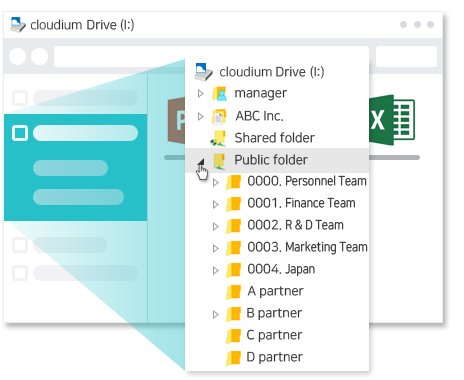
cloudium can manage the account depending on each subcontractor!
If the subcontractor connects to the system, the subcontractor’s staff can check only the already-set folder and file. Since it is possible to set the policy for the document not to be saved in the local PC of the subcontractor personnel, it is effective in preventing the document spill.
You can cooperate without worry because it also manages the history automatically.

Various data arising when you push forward a new project is also the precious intellectual asset of the company.
If it is hard for you to make the department newly and keep the data, solve them simply by cloudium.
You can constitute by TFT, systematically manage all data arising from TFT, and secure the TFT outcome by sharing the data smoothly if you just set the access right for talented persons appropriate for the project.

You can share the global document constantly for 24 hours 365 days by cloudium
Since cloudium is subject to the same document management and security policy anywhere in Korea or abroad, and facilitates the detailed history management on the main events such as the registration, modification, and deletion of the document, you can manage the document systematically without the physical distance and relation.
Since all documents are assorted by overseas branches and registered in Cloudium, you can find the necessary document regardless of time and place and if you upload the file in accordance with the group which should create and share each sharing folder between the headquarter and department, headquarter and branch, branch and branch, you can share the documents conveniently.
If you use the external URL link that set the reading period, reading number, password, and maximum number of available PC in detail, you can smoothly conduct the document cooperation with overseas partners and customers regardless of the size of file and the place.
You will no longer sleep fitfully when conducting the document cooperation with overseas corporations/partners.
cloudium support environment
Windows XP / 7 / 8 / 10
32bit / 64bit OS
Android / IOS
Korean, English, Japanese, Chinese
* HA / DR